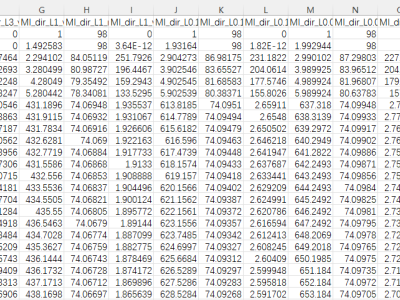
Data Format: The format of the dataset is CSV format.
- Size of Dataset: The size of the dataset is 3.84 Go with 7,068,103 rows and 18 columns.
- The summary of the attributes:
1) Date: Date of the event, in the format MM/DD/YYYY.
2) Time: Time of day, expressed in 24-hour format HH:MM.
3) Timezone: Time zone specified during processing.
4) MACB: Associated with actions performed on a file in a file system: M for modification, A for access, C for change, B for creation.
5) Source: Short name of the source.
6) Sourcetype: More detailed description of the source.
- Categories: